מאמרים מאת יוסי שביט
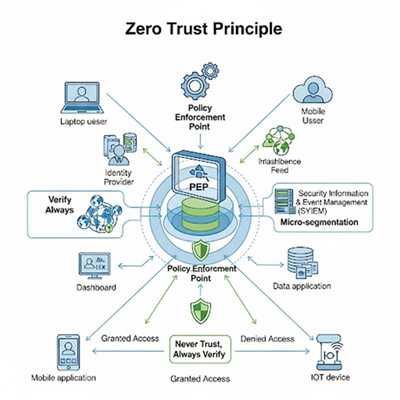
In cybersecurity for industrial control systems and OT networks, we increasingly recognize and assume that the attacker will find their way into the OT network, and therefore we must adopt a Zero Trust policy. In this article I published, I will explain how to implement this in industrial control systems, which represent the soft underbelly of cyberattacks in industrial plants https://online.fliphtml5.com/iawl/zift/?fireglass_rsn=true#p=44
קרא עודThis article seeks to examine a systemic issue that repeatedly arises during my site visits to industrial facilities: the lack of clear responsibility for cybersecurity within industrial control systems and OT networks. Yosi
קרא עודIn today’s interconnected industrial landscape, the boundaries between IT and OT environments have become increasingly blurred. Industrial Control Systems (ICS) and other Operational Technology (OT) environments, which once relied on physical isolation for security, are now deeply integrated with enterprise networks, cloud systems, and remote access capabilities. This integration brings operational efficiency but also unprecedented cyber risks. Yosi
קרא עודModern swimming pools, especially large public or industrial facilities, increasingly rely on Industrial Control Systems (ICS) to manage water treatment, disinfection, and chemical balancing. These systems often control hazardous materials such as hydrochloric acid and hypochlorite, or other toxin materials used for pH regulation. While automation improves efficiency and safety under normal conditions, it also introduces significant cybersecurity risks.
קרא עודDuring my visits to industrial plants that contain numerous industrial control systems and SCADA systems (ICS) operating within segmented and protected OT networks, the question often arises among plant personnel whether it is advisable to move data to the cloud or remain in an on-prem configuration. Since these industrial plants are designed to generate profit, I do not find it appropriate to restrict them or prevent cloud adoption solely for cybersecurity reasons. My approach is to enable the business and support cloud migration when it demonstrates profitability, but to do so with great caution, implementing appropriate security measures to address cybersecurity concerns and the exposure surfaces identified throughout the cloud-migration project.
קרא עוד