מאמרים מאת יוסי שביט #Zero Trust in ICS
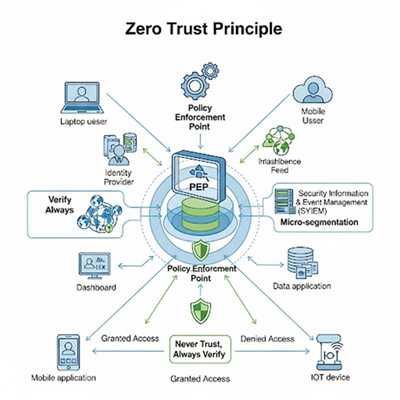
In cybersecurity for industrial control systems and OT networks, we increasingly recognize and assume that the attacker will find their way into the OT network, and therefore we must adopt a Zero Trust policy. In this article I published, I will explain how to implement this in industrial control systems, which represent the soft underbelly of cyberattacks in industrial plants https://online.fliphtml5.com/iawl/zift/?fireglass_rsn=true#p=44
קרא עוד